Secure Protocol Layers Improved Performances (SPLIP)
This page describes the SPLIP feature introduced with SAMA5D2 SoCs. It combines both the Atmel AES and SHA hardwares so crypto data are (de)ciphered and authenticated at the same time. Indeed, those crypto data are processed in parallel, not in sequence, by the two hardware accelerators. Also the SPLIP feature reduces the system bus usage since the crypto data are now sent only once to the AES hardware. Those crypto data are automatically and internally sent from the AES to the SHA hardware, without going through the system bus a second time.
SPLIP has been used in the Linux kernel to implement hardware accelerated drivers for the authenc(hmac(shaX),cbc-aes) crypto algorithms. Those algorithms are mainly used in secured network protocols such as IPSec of SSL.
SPLIP support in Linux is currently available only for SAMA5D2 SoCs.
The Linux kernel version is
4.9.0-next-20161222+.
Enabling SPLIP support
Entering the Linux source directory:
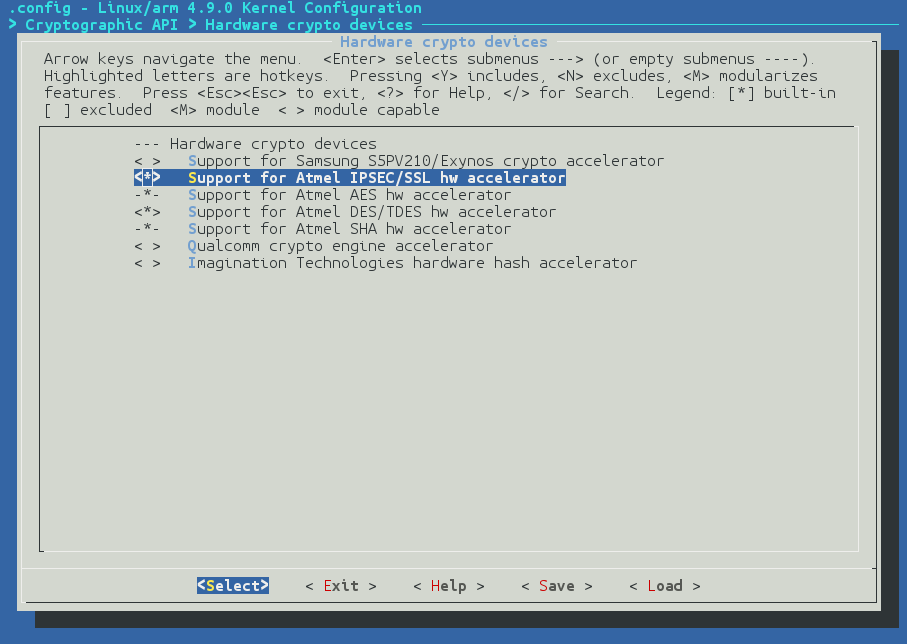
Cryptographic API --->
Hardware crypto devices --->
Support for Atmel IPSEC/SSL hw accelerator
Please note it selects the dependencies to the AES and SHA hardware accelerators:
Enabling IPSec support
Some kernel options need to be selected:
Networking support --->
Networking options ---->
Transformation user configuration interface [CONFIG_XFRM_USER]
PK_KEY sockets [CONFIG_NET_KEY]
TCP/IP networking [CONFIG_INET]
IP: advanced router [CONFIG_IP_ADVANCED_ROUTER]
IP: policy routing [CONFIG_IP_MULTIPLE_TABLES]
IP: AH transformation [CONFIG_INET_AH]
IP: ESP transformation [CONFIG_INET_ESP]
IP: IPComp transformation [CONFIG_INET_IPCOMP]
IP: IPSec transport mode [CONFIG_INET_XFRM_MODE_TRANSPORT]
IP: IPSec tunnel mode [CONFIG_INET_XFRM_MODE_TUNNEL]
IP: IPsec BEET mode [CONFIG_INET_XFRM_MODE_BEET]
The IPv6 protocol ---> [CONFIG_IPV6]
IPv6: AH transformation [CONFIG_INET6_AH]
IPv6: ESP transformation [CONFIG_INET6_ESP]
IPv6: IPComp transformation [CONFIG_INET6_IPCOMP]
IPv6: IPsec transport mode [CONFIG_INET6_XFRM_MODE_TRANSPORT]
IPv6: IPsec tunnel mode [CONFIG_INET6_XFRM_MODE_TUNNEL]
IPv6: IPsec BEET mode [CONFIG_INET6_XFRM_MODE_BEET]
IPv6: Multiple Routing Tables [CONFIG_IPV6_MULTIPLE_TABLES]
Network packet filtering framework (Netfilter) ---> [CONFIG_NETFILTER]
Advanced netfilter configuration [CONFIG_NETFILTER_ADVANCED]
Core Netfilter Configuration --->
Netfilter Xtables support (required for ip_tables) [CONFIG_NETFILTER_XTABLES]
IPSec "policy" match support [CONFIG_NETFILTER_XT_MATCH_POLICY]
Cryptographic API --->
Select algorithms you want to use...
Encrypted Chain IV Generator [CONFIG_CRYPTO_ECHAINIV]
IPSec is protocol suite used to create host-to-host, net-to-host or net-to-net secured connections by authenticating and encrypting each IP packet.
IPSec relies on two main protocols, either AH or ESP, each being used in either transport or tunnel mode.
Authentication Header (AH) versus Encapsulated Security Payload (ESP)
Typically, AH and ESP are independent and not used together in a given IPSec connection. Then both lay directly on top of the IP header in the network protocol stack. Besides both AH and ESP guarantee
origin authenticity, integrity protection of IP packets, those packets being digitally signed by the sender.
Replay attacks can also be detected hence discarding faulty IP packets by checking a 32bit sequence number.
However only ESP provides
confidentiality protection by encrypting the IP packets. Also ESP can be configured to "encrypt only" or "authenticate only" the packets but in the common use both cryptographic transformations are applied.
Transport Mode versus Tunnel Mode
Transport Mode creates a secure connection between two endpoints since it encapsulates the
IP's payload only, while
Tunnel Mode encapsulates the
entire IP packet hence is used to create a secured Virtual Private Network (VPN) between two gateways.
Network protocol layout
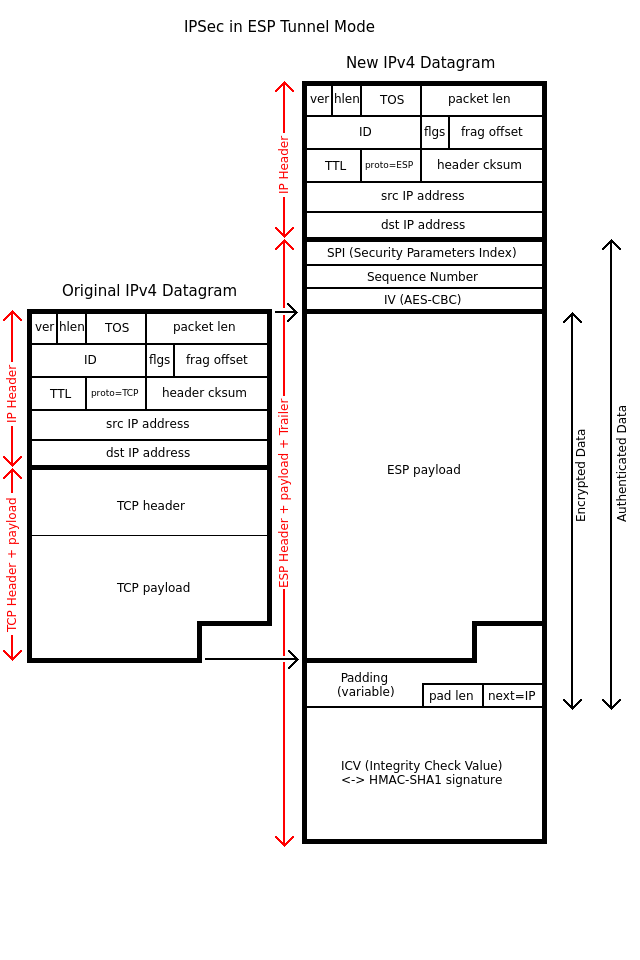
This page is focused on
IPSec in ESP Tunnel Mode. In ESP Tunnel Mode, the entire original IP datagram is encapsulated in a new IP datagram. An ESP header is inserted between the new IP header and the ciphered version of the original IP datagram. This ESP header contains a
Security Parameters Index (SPI) number, which allows to attach the new IP datagram to the right IPSec connection and its associated security parameters (cipher and signature algorithms, ...).
To take advantage of the SPLIP feature, those security parameters are chosen so networks packets are digitally signed with the
HMAC-SHA1 algorithm and ciphered with
AES-128 in CBC mode.
Finally, to measure the network bandwidth with the iperf tool, the
TCP protocol is used on top of the original IP header to provide the best connection speed.
Hence the resulting network packet layout is:
StrongSwan is an open-source IPSec-based VPN solution. In the following example, we created a connection between two hosts, a
SAMA5D2 Xplained board and a PC desktop under Ubuntu, with IPSec in ESP Tunnel Mode.
PC desktop (192.168.2.254) setup
Install the StrongSwan package:
~$ sudo apt-get install strongswan
Check/edit the IPSec configuration file (/etc/ipsec.conf):
~$ sudo cat /etc/ipsec.conf
config setup
conn %default
ikelifetime=30m
keylife=15m
rekeymargin=3m
keyingtries=3
mobike=no
dpdaction=clear
dpddelay=30
dpdtimeout=120
conn PSK
authby=secret
auto=start
keyexchange=ikev2
ike=aes128-sha1;modp2048
esp=aes128-sha1;modp2048
type=tunnel
left=192.168.2.254
right=192.168.2.1
Restart the ipsec service:
~$ sudo ipsec restart
SAMA5D2 Xplained board (192.168.2.1) setup
On the host, from the buildroot folder run a "make menuconfig" command and select the strongswan package.
~/buildroot$ make menuconfig
Target packages --->
Networking applications --->
strongswan --->
Enable AF_ALG crypto interface to Linux Crypto API
Enable the IKEv1/IKEv2 keying daemon charon

Then run a simple "make" command to generate your
target buildroot rootfs/image.
~/buildroot$ make
Now
on the target, check/edit the IPSec configuration file (/etc/ipsec.conf):
# cat /etc/ipsec.conf
config setup
conn %default
ikelifetime=30m
keylife=15m
rekeymargin=3m
keyingtries=3
mobike=no
dpdaction=restart
dpddelay=30
dpdtimeout=120
conn PSK
authby=secret
auto=start
keyexchange=ikev2
ike=aes128-sha1;modp2048
esp=aes128-sha1;modp2048
type=tunnel
left=192.168.2.1
right=192.168.2.254
Still
on the target, start the ipsec daemon:
# ipsec start
Later, you can check the status of the IPSec connection:
# ipsec status
Security Associations (1 up, 0 connecting):
PSK[1]: ESTABLISHED 9 seconds ago, 192.168.2.1[192.168.2.1]...192.168.2.254[192.168.2.254]
PSK{1}: INSTALLED, TUNNEL, reqid 1, ESP SPIs: ce744834_i c1bb2cd7_o
PSK{1}: 192.168.2.1/32 === 192.168.2.254/32


 Then run a simple "make" command to generate your target buildroot rootfs/image.
Then run a simple "make" command to generate your target buildroot rootfs/image.